Protection Activities Content
Protection Activities
We operate a team dedicated to personal data and a well-organized management system to protect users' personal data systematically and safely.
Protection Activities Menu
Kakao Personal Data Protection PrinciplesKakao Personal Data Protection Principles
Kakao always gives priority to data connectivity, data protection and users’ trust in order to make a better world with technology and people.
In order to provide services based on users' trust, Kakao’s executives and employees are committed to process users’ personal data based on the following principles.
- 1. Kakao repects user privacy and protects personal data at every phase of its services.
We go beyond compliance with laws related to personal data protection, and consider protecting user privacy. Based on Privacy by Design, we introduce and develop preventive measures, inspections, and privacy impact assessments to protect privacy at all stages.
- 2. Kakao discloses its personal data handling process transparently.
We transparently disclose the processing of personal data collected, and the purpose of processing. We also strive to increase practical transparency by providing clear and easy explanations to users so that all users can understand our personal data handling process.
- 3. Kakao collects the minimum personal data necessary for service provision.
We check personal data required for service provision and collect the minimum personal data.
All personal data are collected legally in accordance with applicable laws, in order to prevent unnecessary collection. - 4. Collected data are retained only for as long as necessary and managed safely.
We keep collected data only for the period necessary to provide services, and destroy unnecessary data without delay.
We strive to safely manage stored personal data by applying and strengthening security technologies. - 5. Kakao guarantees users’ right to self-determination.
The right to personal information belongs to the information subject who owns the information. We guarantee the rights that users have as information subjects, and provide functions and processes to exercise them.
- 6. Kakao strives to fulfill social responsibilities.
In line with the development of new technologies and changes in the social environment, we endeavor to implement advanced protection activities necessary for users and to fulfill our social responsibilities.
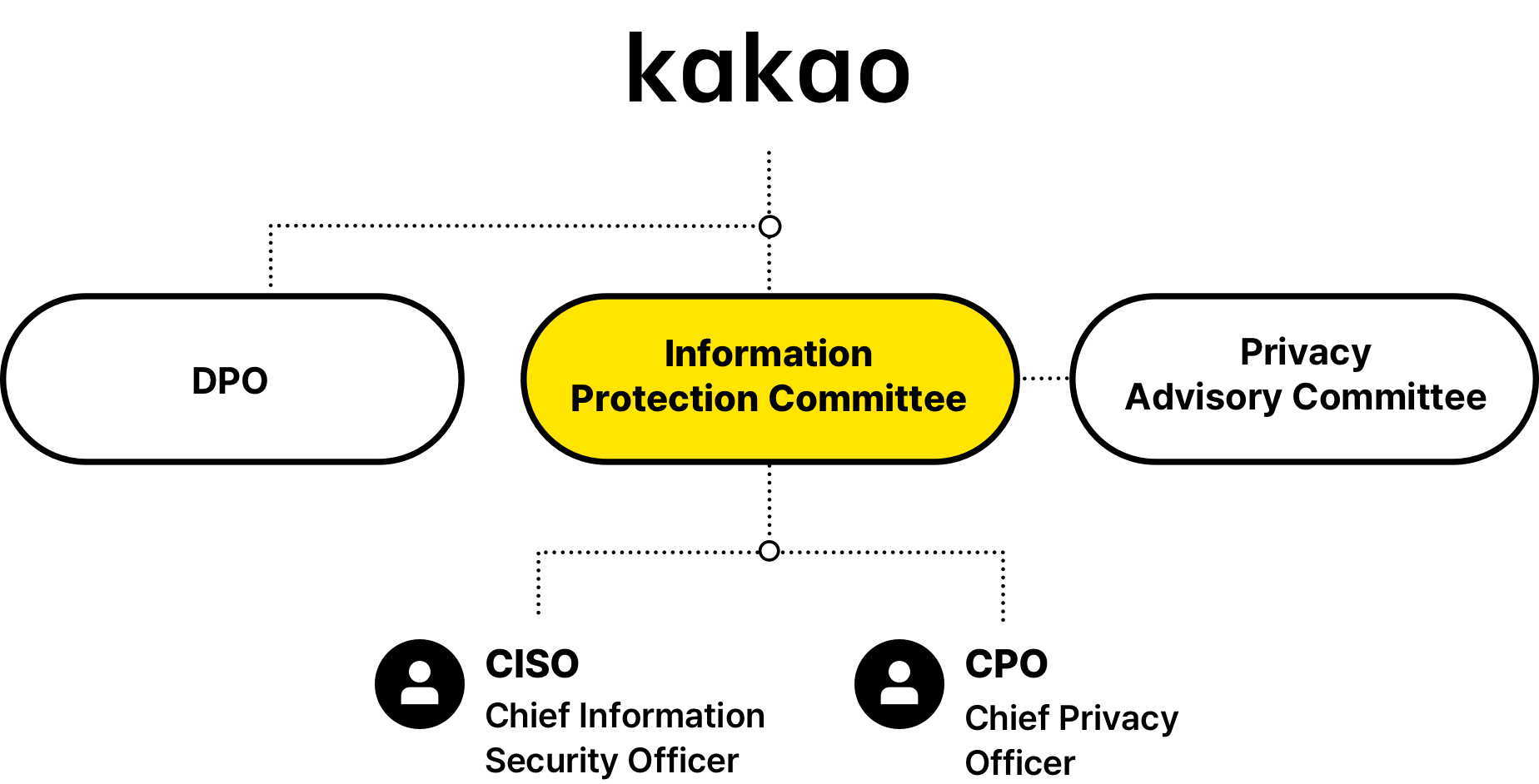
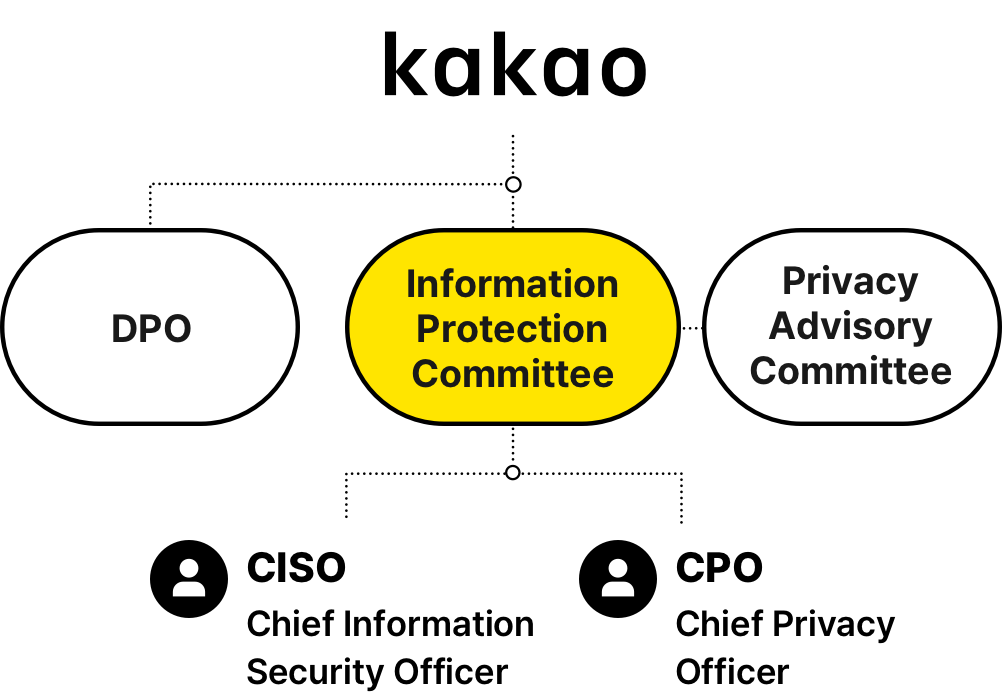
Privacy Protection Organization
Kakao separates CPO (Chief Privacy officer) and CISO (Chief Information Security Office) roles, responsible for heading our data privacy operations and information security operations respectively, to ensure that the company deals with data privacy issues professionally and systematically. The CPO position is assumed by the head of a department (executive) organized for data privacy operations following the Personal Information Protection Act and our internal regulations to ensure his/her qualification for overseeing data privacy operations. The CISO is appointed for expertise on data privacy and information technology following the Information Communications Network Act.
1. Data Privacy Governance
2. Kakao Privacy Advisory Committee
Kakao has operated the Kakao Privacy Advisory Committee composed of Korea’s top privacy experts in an attempt to reflect various perspectives to policies related to the privacy protection of its users since 2014. Consisting of experts with backgrounds associated with data privacy and security including law and academia, the Committee has held held regular advisory meetings to identify regulatory trends related with domestic/overseas privacy issues, and provided well-informed advice to our privacy policy directions.
Activities of the Privacy Advisory CommitteeNew Window3. Data Privacy Policy Organization
Our data privacy policy organization has been up and running since 2018 to safeguard user data and provide better services in so doing. This organization develops Kakao’s data processing policy on the back of practical data processing capabilities and deep understanding of data privacy regulations, and disseminates the data processing policy across working-level organizations.
Personal Information Protection Management System
Kakao’s main priority is user trust. All executives and employees of Kakao are committed to handling users’ personal data based on the following principles.
Kakao performs privacy impact assessments for services provided to users for the secure handling of users’ personal data. Privacy impact assessments are performed through the entire service lifecycle following the Privacy by Design principle. Our main objectives are to review our compliance with applicable laws, including the Personal Information Protection Act, from service planning to change and termination while closely evaluating impact on users’ data privacy to eliminate risks in advance.
- Collection of personal data : Check explicit user consent, collect minimum data required.
- Transmission/storage of personal data : Secure transmission of personal data; encrypt passwords, financial data and location data.
- Use of personal data : Minimum use within business purposes, prevention of the misuse of personal data.
- Transmission and storage of personal data: Safe transmission of personal data, encryption storage of password, financial information, location information, etc.
- Management of personal data processing system : Identification of personal data processing history and permission review, control of unnecessary personal data exposure, logging of personal data processing.
- Provision of personal data : Minimum provision of personal data, securing the transmission of personal data.
- Disposal of personal data : Verify the adequacy of the data to be destroyed and disposal timeframe, and whether they were destroyed safely.
- Termination of personal data processing system : Confirm the termination of personal data processing system and the return of assets.
Our data privacy review and management system is in operation as a follow-up process to assess whether privacy protection activities are properly implemented. The service checklist covers matters on information security certifications and user privacy protection as well as for regulatory compliance concerning the Personal Information Protection Act and the Location Information Protection Act. Our personal data handling personnel management system enables the integrated status management of our personal data processing system, personal data handling personnel, and personal data handling operations.
Kakao ensures that subsidiaries, suppliers, and other-third parties (“outsourcing companies” hereinafter), to whom we contract out our personal data processing operations, implement data privacy measures on par with those of Kakao. We enter into written contracts with these outsourcing companies to stipulate that they abide by the Personal Information Protection Act and Kakao’s data privacy policy, and perform regular reviews on their data privacy operations to ensure they protect data privacy in accordance with the contract signed and applicable laws. To this end, we developed an outsourcing company checklist in line with relevant laws to verify their data privacy policy and protection activities and make sure improvements are made if any non-compliance is identified. Such reviews are followed by comparing the data privacy levels of outsourcing companies before and after improvement to evaluate the effectiveness of such improvements, and the results are reflected in the following reviews to be made when deemed necessary.
Kakao conducts various precautionary inspections such as security vulnerability checks, security coding, and code review in order to maintain the level of security above that required by law. All Kakao services are periodically checked for vulnerabilities from the pre-planning stage, before the service release, to the closing stage. In addition, in the development stage, code review procedures and safe security coding are conducted to address technical vulnerabilities. Kakao will exert the utmost efforts to provide secure service by enhancing security and proactively responding based on new trends and technologies.
Kakao's personal data processing system and membership database are maintained under strict access control. Only the minimum number of authorized users can access the systems after going through a strict process. Each responsible person judges the necessity based on the scope of work, grants access, and monitors authorized personnel and intrusion detection system that blocks all unauthorized access attempts. Kakao has installed, managed, and operated server firewalls to safeguard critical data.
Kakao performs log analysis and monitoring on personal data access and handling, while also retaining the history of access right request, change, and deletion. Unnecessary permissions are immediately canceled through periodic reviews. As a leading data company, Kakao is equipped with data privacy pledges required from its employees. In order to enhance privacy awareness among employees, Kakao offers privacy protection training more than twice a year. Moreover, malware scanners are installed on employees' computers to detect and remove malware.
Kakao's Security Control Center operates a dual security control system that is monitored 24/7 by both Kakao's own security officers and independent security experts. Kakao closely analyzes security events and attacks that occur in its systems and networks to detect and respond to potential threats. These efforts safeguard Kakao's many services and customer data, and prevents security incidents.
Despite thorough pre- and post-control activities, we prepare a personal information leakage response manual in case the user's information is leaked, and according to the relevant laws, we have a personal information leakage response procedure that informs the user and reports it to the authorities. In addition to notifying users of accidents and reports, the personal information leakage response procedure includes information on the company's countermeasures, contact information for consultation, and damage relief procedures to minimize damage to users.
Information Protection Certification
Information protection certification is a system that grants certification after examining whether information protection management systems established and operated by a company to protect its major information assets meet certification standards. Kakao protects users' information assets through information protection management system certification.
The Personal Information & Information Security Management System (ISMS-P) Certification is a certification system for a comprehensive management system including administrative, technical, and physical protection measures and a series of measures related to the processing and protection of personal information of personal information processors to ensure the safety and reliability of information and communications networks.
Certification Scope : Operation of Kakao Services(including Kakao Certificate and E-Document Service)
Effective Period : Feb 1, 2023 ~ Jan 31, 2026

Information Security Management System (ISMS) Certification is a certification system that examines whether a series of measures and activities established, managed, and operated for information protection meet the certification audit criteria. Kakao has obtained certification for 'Kakao DataCenter', which is responsible for safely managing user data, and maintains the certification through continuous management.
Certification Scope : Kakao DataCenter Operation
Effective Period : Nov 20, 2024 ~ Nov 19, 2027

ISO/IEC 27001 is the international standard for information security management systems, administered and managed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It is an international standard that stipulates the requirements of a management system to set security goals and achieve them in order to safely preserve and manage organizational information. Kakao has acquired certification for its company-wide services and is maintaining the certification through continuous management.
Certification Scope : Kakao Services
Effective Period : July 7, 2024 ~ July 6, 2027


Privacy Protection in Services
Kakao Services are equipped with functions and technical measures to minimize the exposure of personal information and to safely protect users' personal information.
In addition to the main profile in KakaoTalk which is open to public view, you can create up to three multi-profiles and make specific profiles public only to the people you want. Even for the profile for which the audience is set to public, you can choose not to expose it to unwanted people.
By exposing whether the digital signature of a KakaoTalk user has been verified in Wallet, the user’s reliability is guaranteed. Also, whether or not a real name will be shown can be decided.
KakaoTalk offers ‘Globe Signal’ and ‘Talk Siren’ to control user damage from phishing crimes by impersonated acquaintances. These functions display an alert pop-up when a non-friend attempts to enter a chat room for conversations, and emphasize a precaution against money requests on the top of the chat room after he/she enters the chat room.
If the other party talking to you is a subscriber of the national (Korean) telephony, an orange profile image will be shown as a precaution to help users recognize the possibility of impersonation. If the person is a subscriber of the foreign (other than Korea) telephony, an orange globe-like profile image and the country information of the phone number to which the person is subscribed will be displayed.
We provide various security settings to secure users’ Kakao Account information.
We provide the account security diagnosis function to check if your Kakao Account is safe. The system diagnoses the safety status according to the status of a user’s account, and provides guidance on what security activities are required based on the results of the diagnosis. That way, users can improve the security of their accounts. If the risk level is “High”, users are advised to actively participate in security activities which can protect their accounts.
If unusual usage is detected with your Kakao Account, additional authentication to confirm your identity is requested, or account protection measures are imposed. Through these detection activities, you can safely use your Kakao Account even if your personal information has been leaked somewhere.
We provide strengthened security settings to help users protect their Kakao Accounts. Even if your password is leaked, you can use your account safely in the most reliable way by setting two-factor authentication that allows you to log in after completing additional authentication, as well as country-specific login restrictions that allow login only from countries that you have allowed.
When you use other services, you can check required and optional personal information items and manage connected services.
Kakao Login is a social login service that allows you to use various services with your Kakao Account. You can check the personal information and purpose of use necessary for using other services, and choose whether or not to provide optional items. Providers of services linked through Kakao Login can only access information that you have directly agreed to provide.
You can view the list of services connected though Kakao Login and also withdraw your agreement from services you no longer use. When you disconnect your Kakao Account from a service, the service can no longer access your personal information.
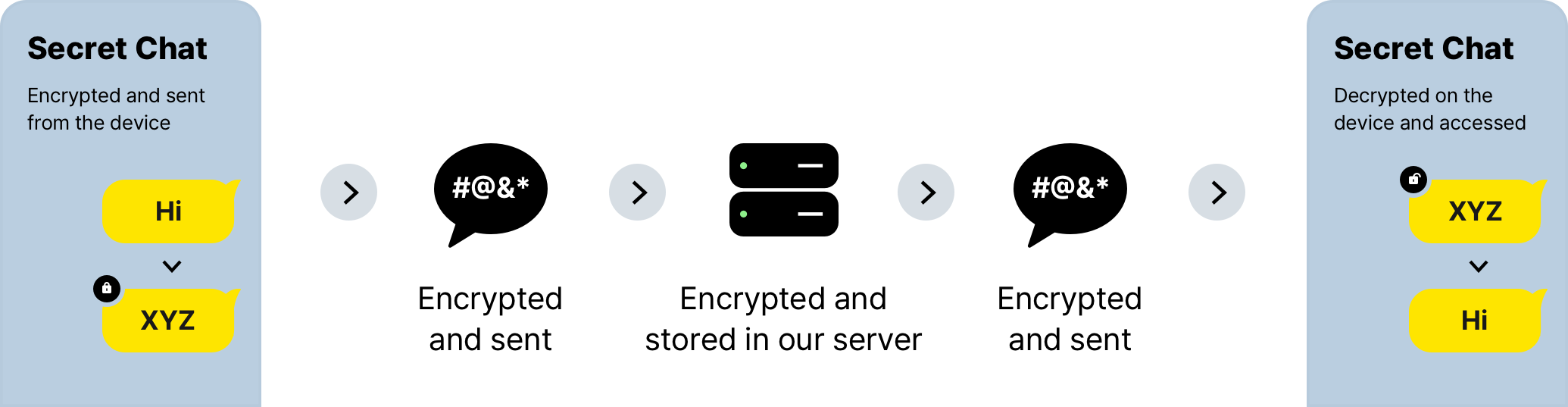
KakaoTalk’s secret chats deploy end-to-end encryption technology to provide stronger user data protection. This technology transmits encrypted messages and stores decryption keys used to decipher such messages only at individual terminals. This fundamentally prevents the decryption of user data encrypted and stored in our server unless the terminals are directly analyzed.
Your precious gift message written in KakaoTalk Gift is managed safely using the encryption technology so that it can be shown only to the person who receives the gift.
When a user receives a gift from a blocked friend, the name of the sender and the content of the gift are automatically locked in order to protect the user from unpleasant gifts. When the user unblocks the sender, he or she can check the sender’s name and the gift, and use it like a normal gift. If the sender is not unblocked by the deadline, the gift will be rejected automatically.
In other Gift services, a sender usually enters the address of a recipient. But in KakaoTalk Gift, a user can send a gift even if he or she does not know the recipient’s address. The recipient can enter his or her address directly in the app without disclosing it to the sender. In this way, gifts can be sent and received without disclosing personal information between chatroom members who are not very close and yet share similar interests.
When using Gift Code and Open Chat Gift, you can safely exchange gifts with other people without disclosing your KakaoTalk nickname and real name.
User information is further protected by applying reinforced protection measures such as 2-step authentication.
2-step authentication is required for all sellers so that they can be protected from the risk of account theft such as credential stuffing.
Sellers can view a customer’s personal information in the “Preparing for Delivery” stage when they need to view the customer’s order (personal) information for delivery processing. However, after the delivery is completed and the customer confirms the receipt of the gift, personal information is masked to prevent sellers from accessing them.
In addition, a seller’s authority is divided into Master and Manager, and the master is authorized to retrieve the authority of an employee who has left the company (manager). Access records and permission change histories are also saved to reinforce accountability in case of any personal information related issues. Furthermore, sellers can disclose their personal information processing policy in Kakao’s service page.